Who are the first hackers?
 Interestingly, modern schoolchildren and students of technical universities realize that the history of computers did not begin with Bill Gates, and the first hackers did not hack servers, and wrote … games for entertainment?
Interestingly, modern schoolchildren and students of technical universities realize that the history of computers did not begin with Bill Gates, and the first hackers did not hack servers, and wrote … games for entertainment?
Let’s start from the middle, because for a correct logical narrative, one would have to start from the 50s of the last century. And today, few will master this information, and not because it’s boring, but because it’s all such junk, the first “humanized” programming languages Beisk, Fortran, Kobol and even Pascal existing today. They are as ancient as the real human languages, Latin and ancient Greek, and, thank God, most techies do not need to learn them. Therefore, this article will devote to the history of hacking. What do you think, who, for what and how hacked servers in the middle of the last century? Nobody and for what, since then there were no servers. And there were curious students at the Massachusetts Institute of Technology (MTI), where in the late 50s, mathematics students (the concept of “student programmers” did not exist yet) organized their club for railway technical modeling. This was not for pleasure, but for solving student tasks related to the construction of a model of the railway and its cargo flow.
The club had two sections, the first one today would be called the design one, since mock-designers and future engineers — electricians, mechanics, dispatchers — worked in it. But the second part of the group was the most creative and fanatical – it created a confused labyrinth of codes (programs), which is the main thing in the project, its filling. Like apple pie filling, otherwise it will not be a pie, but a loaf. Spending a huge amount of time, mostly nightly, as the daylight was shared between real programmers, students of the second section endlessly mounted the system. And they were touched when they managed to get a plausible result. After that, they could warm up.
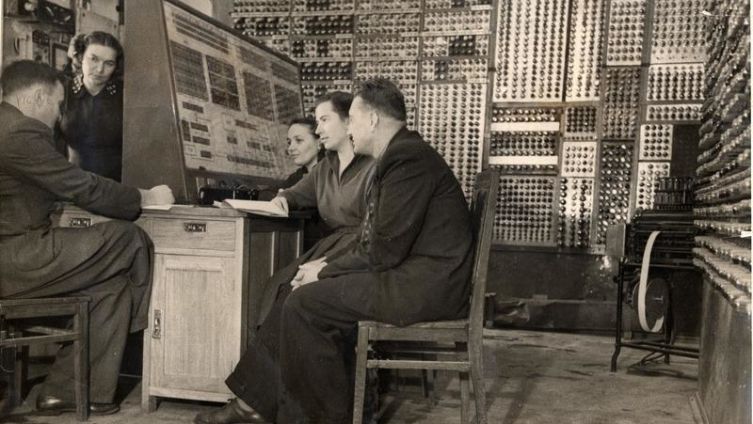
This sports term, in English sounding like warm up, meant that the equipment was not yet ready for the programming process, it must be warm up – warm up. And if you play with the parameters of the resulting program, then you can make a lot of it … that for this process a new term “hack” was needed, which in the original meant “hack” or “blooper”. Students of the club considered such mistakes of their work absolutely unnecessary from a practical point of view, and they called themselves Hackers, hackers. In a word, they were completely harmless, unless they drove a program on a computer longer than the time set for this. In 1958, the TX-O computer entered the scene, which later became the super-famous IBM company, in which for the first time instead of electronic lamps and switches they began to use transistor circuits. Moreover – oh miracle! – the computer had a display on lamps, as in televisions of that time, which not everyone had even in America. And TX-O also had a couple of wonderful devices: audio output and light pen. So for the first time Bach’s music was played by a computer (the poor composer turned upside down), and for the sake of jokes, students also composed a program for converting Arabic numerals to Roman ones. Interestingly, when satisfied inventors showed the “digital program” to the math teacher, he said: “Oh, my God! Who needs it? ”That is, it showed the absolute applied uselessness of the brainchild. The teacher was short-sighted, other professors fussed and became hackers themselves. The first of them invented the Labyrinth game, where a mouse ran around a rectangular labyrinth, expressed by a round light spot, and the light spots of a triangular type represented pieces of cheese. Another professor, being a little tipsy, complicated the program: the mouse looked for and drank martini glasses, and its movement from the first glass to the next became more and more loose. The professors played their toys with no less enthusiasm than their students in their own. When the first PDP (Programmed Data Processor), created by a graduate of the institute, Kenneth Olsen, was brought to the institute to replace the bulky TX-O, everyone applauded – this machine was as big as three refrigerators put together. It was a real revolution, which led to the appearance of familiar mini-computers.
The machine itself requested that a couple of completely new games be written to it. Professor Marvin Minsky, who was engaged in a serious topic – artificial intelligence, wrote a program (then this process was called coding), which created three colored spots on the screen using a random number sensor. And then it was possible, by multiplying them, to create various ornaments and effects. Minsky’s program, called Minskitron, fell in love with his colleagues, who simply meditated on it, and students. One of the latter, Stephen Russell, who would today be called a botanist, adored science fiction and unscientific fiction and horror films. He was also computer obsessed and, taking Minskitron as a basis, created the simple but very effective game “Space War”. Two players could take part in it, trying to destroy the enemy army with rockets of space ships.